Download the user manualAdministrator’s guide for corporate version of “Antiplagiat.Network” system
Introduction
This manual is intended to familiarize you with the means of work in the .
The manual contains information about the purpose, capabilities, features of the system, as well as a description of the actions that provide check of text documents for the detecting reuse.
Terms and definitions
|
Term |
Definition |
|---|---|
|
System (service) |
Online tool for working with text documents with user interface on the web-site. |
|
Text similarity |
A fragment of the document text that contains the text or a fragment of the source text and is not formatted in accordance with quotation rules |
|
Text recycling |
A fragment of the document text that contains the text or a fragment of the source text, the author or co-author of which is the author of the checked document |
|
Quotes |
A fragment of the document text that contains the text or a fragment of the source text and formatted in accordance with the rules of quotation, with full bibliographic information about the source. Also quotes include common expressions, bibliography, fragments of text found in sources from the collections of regulatory documents. |
|
Text similarity percentage |
The proportion of all found similar text in relation to the total size of the checked document in characters |
|
Text recycling percentage |
The proportion of all found text recyclings in relation to the total size of the checked document in characters |
|
Quotes percentage |
The proportion of all found quotes in relation to the total size of the checked document in characters |
|
Originality percentage |
The proportion of all document text fragments that were not found in the sources used for check, in relation to the total size of the checked document in characters |
|
Report |
The result of checking the text for reuse:
|
|
Report share |
The ratio of the volume of matches that is taken into account within this source to the total volume of the document. That is, if the same text was found in several sources, it is taken into account only in one of them. When summing up the shares in the reports for all sources, a percentage of "Similarity" is obtained. |
|
Text share |
The ratio of the volume of matches of the source text to the volume of the document. The shares in the text by sources are not summed up when calculating the total percentage of matches. |
|
Report blocks |
The number of text similarity blocks from the source, taking into account the intersections of all found sources. |
|
Text blocks |
The number of text similarity blocks from a source without regard to other found sources. |
|
Collection (search module) |
The software module of the corporate version of the system , implementing the search for text reuse. The module uses a search index or a special computational algorithm to build reports. The system can have several collection. Search modules may differ in purpose, for example: Once you have access to several search collections, you can build both individual reports and a single report for all search collections. Some collections perform searches across specialized databases with the casts of the texts of the source documents, but to obtain access to the selected search module doesn't mean getting access to the full texts of the documents it can find this collection. In the received reports, links to the documents will be indicated (their names will also be given), and when viewing the source text, it will contain fragments that coincide with the document being checked. |
|
Browser |
Software that allows users to view pages on Internet sites and access files and software associated with those pages. For example, Mozilla Firefox, Google Chrome, etc. |
Purpose and conditions of use
The service is designed to check text documents for plagiarism. As a result of the scan, users receive text reuse reports. The report contains information on the sources and indicators of text similar to source, as well as detailed information with the indication of those fragments of the checked document that have been identified as text similarity. The identification is accompanied by the presentation of the matching text fragment of the borrowing source and/or the reference to the original (URL). As a result of the document check, the user can determine which part of the document is written independently and which part is reused.
To use the service you need:
- Connect to the Internet;
- Install a browser or use the browser of one of the most common types built into your operating system (MS Edge version 97 and above, Mozilla Firefox version 90 and above, Opera version 78 and above, Chrome version 92 and above).
The results of work with the system are not the basis for claims of copyright violations, the service is aimed at use only for information purposes. In other words, we do not declare that a particular text is plagiarism, but only inform you about the presence of the same or similar text fragment. It is possible that when working with the service, you will find the text copied from other sources, including the possibility that the downloaded document is the original source. In any case, when working with the service, be careful, try to be objective and do not rush to conclusions. Remember that the service is only a tool of work, and only the user can give a real assessment to the document.
Preparation for the start
Workplace
To prepare the workplace when working with the system it is enough to open a browser. To work with the service, browsers of the most common types, such as MS Edge version 97 and above, Mozilla Firefox version 90 and above, Opera version 78 and above, Chrome version 92 and above, can be used.
To get started, go to the service website by typing in the address bar of the browser address you received by e-mail from the administrator of the company.
So, we have a ready workplace:
- files downloaded to your computer;
- the browser is open;
- the service's website page is opened in the browser.
Log in and log out from the system
To access the system, use the login form. To do this, click on the "Log in" link in the upper right corner of the page.
If you do not remember the e-mail that you used for registration in the system, then you can use the "Remember e-mail" function on the login page. You will see a window for entering registration details from the old site: login and password. If you enter your login and password correctly, you will see the e-mail you used for registration on the old site.
Fill your credentials into the opened login form. Click on the "Show password" button, if you want to check the correctness of the password. Click on the "Log in".
After log in the icon "Menu" will be displayed on every page of the website in the upper right corner of the page. When you click on the icon, the navigation through the sections of your account will be available. To the left of the "Menu" icon you will see a brief information about yourself: the role in the system and e-mail. Figure 4 depicts an example for the "Expert" role.
To log out from the system, click on the "Menu" icon and then select "Log out".
Role change
If your system administrator has assigned you more than one role, you will see an arrow next to the role name located at the top of the page. Click the name of the current role to view the full list of roles available to you.
To change a role, click its name in the drop-down list of roles. After that, the page will change the name of the current role, and you will be redirected to the user account for this role. Please note that only one role is available at a time.
Profile
To go to your profile, click on the "Menu" and select the "Profile" tab.
In the profile you can review your credentials. User's data can be changed only by the company administrator.
Two-factor authentication
Two-factor authentication (2FA) is an additional security measure for an administrator's account. 2FA is implemented by linking your account to a 2FA application, which must be installed on a mobile device (smartphone or tablet).
You can install any 2FA application, but we recommend using Google.Authentificator (iOS, Android).
Applications generate one-time digital codes that will need to be entered before performing the following actions with users:
- User creation (after clicking the "Add" button on the user creation page);
- Batch creation of users (after clicking the "Import" button on the administration page);
- Changing a user (after clicking the "Change" button on the page for changing a user);
- Sending a password to the user (after clicking "Send passwords" in the action confirmation window);
- Unblocking the user (after pressing the "Unblock" button in the action confirmation window);
- User recovery (after pressing the "Restore" button in the action confirmation window);
- Impersonating into a user (after clicking the "Log in" button on the "Administration" page).
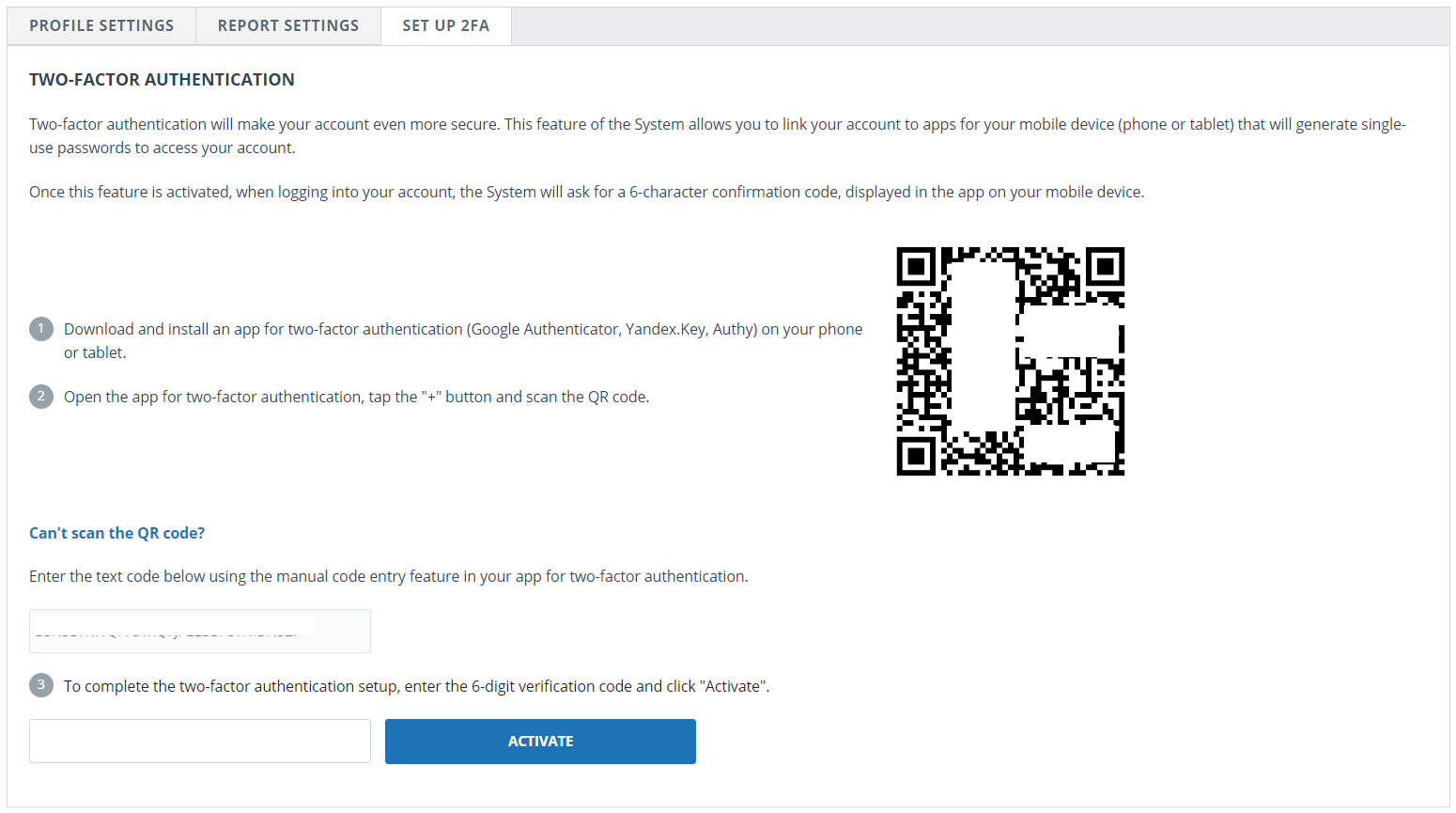
In order to set up 2FA, follow these steps:
- Install the 2FA application on your mobile device (smartphone or tablet);
- Scan the QR code using the application, or enter the text version of the code;
- After the application generates a numeric code, enter it in the field at the bottom of the page and click the "Activate" button;
- Click the "Close" button in the window that appears with a message about the successful connection of 2FA.
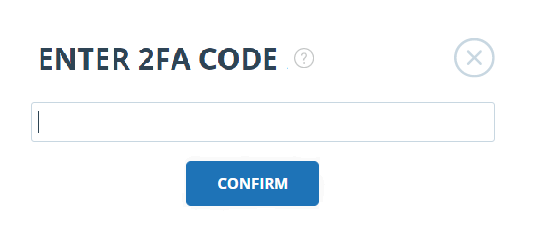
A window for entering 2FA will appear when performing actions with users. You will need to enter the numeric code from the application and click the "Confirm" button.
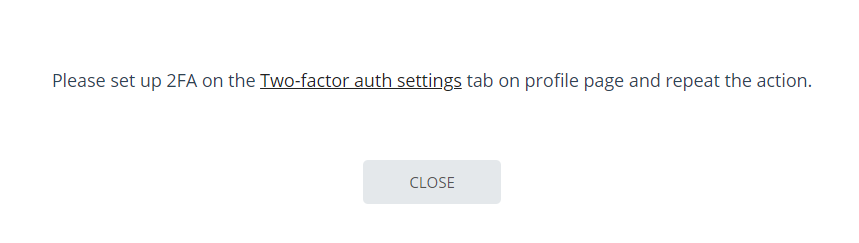
If you have not previously linked your account to the 2FA application, then a window will appear with a message about the need to configure 2FA when you perform an action with the user. The message will contain a link to the "2FA Settings" tab.
The 2FA functionality is enabled by default. 2FA is activated for free.
Important! If the administrator loses access to the 2FA application on a mobile device, then the 2FA settings can be reset by .
employees.
To reset 2FA, contact your organization's root system administrator. If you are a root administrator and you need to reset the 2FA administrator, then write an email to our Customer Care Service support@.ru.
Customer Care Service
If you do not find answers to questions about the system, please contact Customer Care Service. To do this, click on the "Menu" in the upper right corner and select the "Customer Care Service" tab. The system opens a window with a form to send the case.

Enter your question in the "Message" field and click on the "Send" button. Our experts will respond to your request to the e-mail, which was used to log in.
Adding a website
Our Internet search module performs a check on the already indexed sites of the web. If you find an interesting site or resource that is not included in the Internet search module, you can add it to our search module. This will allow you to build more complete and reliable reports for check through the Internet search module.
To add a website for indexing, click on "Menu" and select "Add website". Copy the link in the URL field and click "Add". You can also leave a comment about the site to which this link leads, for example, that this site is an open e-library or abstracts site.

If the site you specify is already known to our system, you will receive the message: "The Site has already been processed by our system".
Please note that the new website will be placed in the Internet search Module according to the order of the indexing queue.
Administration
View the list of users
To view the list of users, click on "Menu" icon and select "Administration" section.
The list of company users appears with the information about them.
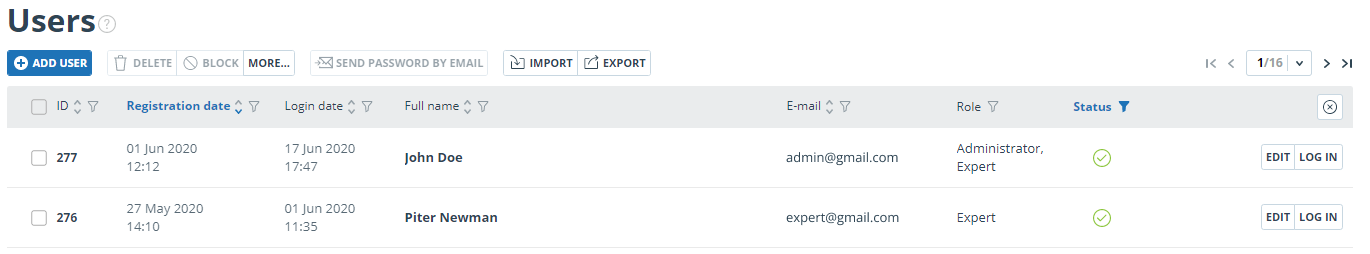
First time you log in, you will see two users with Administrator role (learn more about roles in the "User roles" section):
-
Support Service – an employee of
company, who is responsible for supervision over system efficiency, troubleshooting and assistance to users of the company.
- Root administrator - administrator of your company, created by Customer Care Service during company activation.
User roles
The system provides the following user roles:
- Administrator - user of system, who is responsible for administration of usage of the purchased product.
- Expert - user of system, who checks text documents.
- Supervisor - user of system, who can view all actions of all users of purchased system.
- Moderator – system user who manages the software products in terms of the network for each separate subdivision that is being activated.
Availability of these roles depends on your system configuration.
User search
For convenience of usage of the list of users, the system provides search for users by id, e-mail, name, registration date, login date, role and status.
By default, list of users is sorted by registration date in descending order. You can change sorting order in the header of the table, the direction of the arrow will change, pointing to the sorting method, and the column, which is currently sorted, is highlighted in bold.
Impersonation of administrator into user's workspace
You can impersonate into account of any company's user. To do this, click on "Log in" button in row with the selected user. Page with user's workspace under his/her login will open in the new tab. Administrator can access all features and documents of this user.
You can impersonate in only one user. To exit the impersonation mode, click on "Log out" in the user menu. After that, the administration page will open, you can continue to work with the system on your own.
Creation of a new user
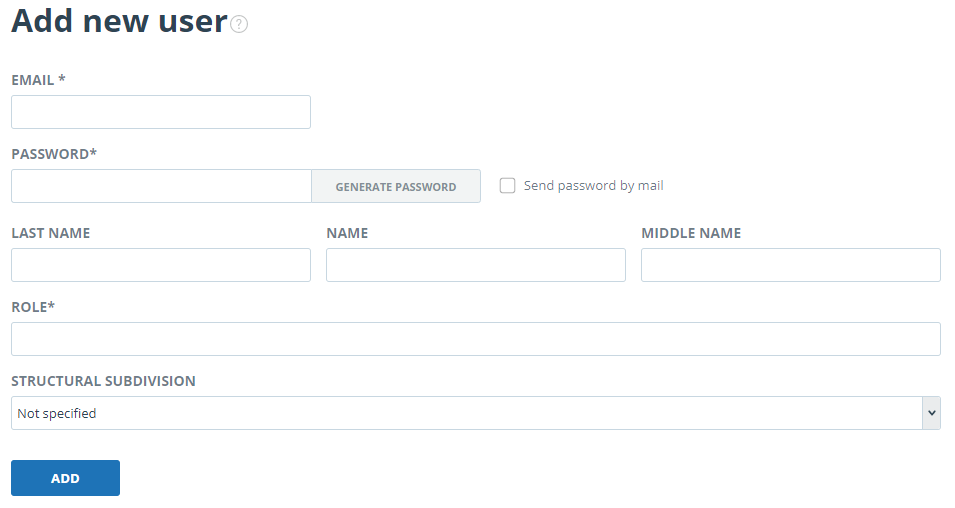
To add a user of the system, click on the "Add user" button in the top menu. Fill in the fields of the opened form and click "Add". The new user will be displayed in the top row of the table.
E-mail, password and role are the required fields.
Multiple roles can be assigned to a user in the system. Depending on the roles assigned, the user can switch between them and perform the activities that are specific to the role.
The created user will receive a link sent to the specified e-mail for setting the individual password. If you uncheck the "Send password by e-mail" checkbox, then the link for password setting after clicking the "Add" button will not be sent. To postpone or resend the link to the password setting page, use the Editing Users section.
Editing users
To change the information about a user, click on the "Edit" button in the row of the appropriate user. The edit user's account window will open.
The Administrator can change the e-mail, user information, oblige the user to change the password (send a link to the password setting page), change or add another role to the user in the system.
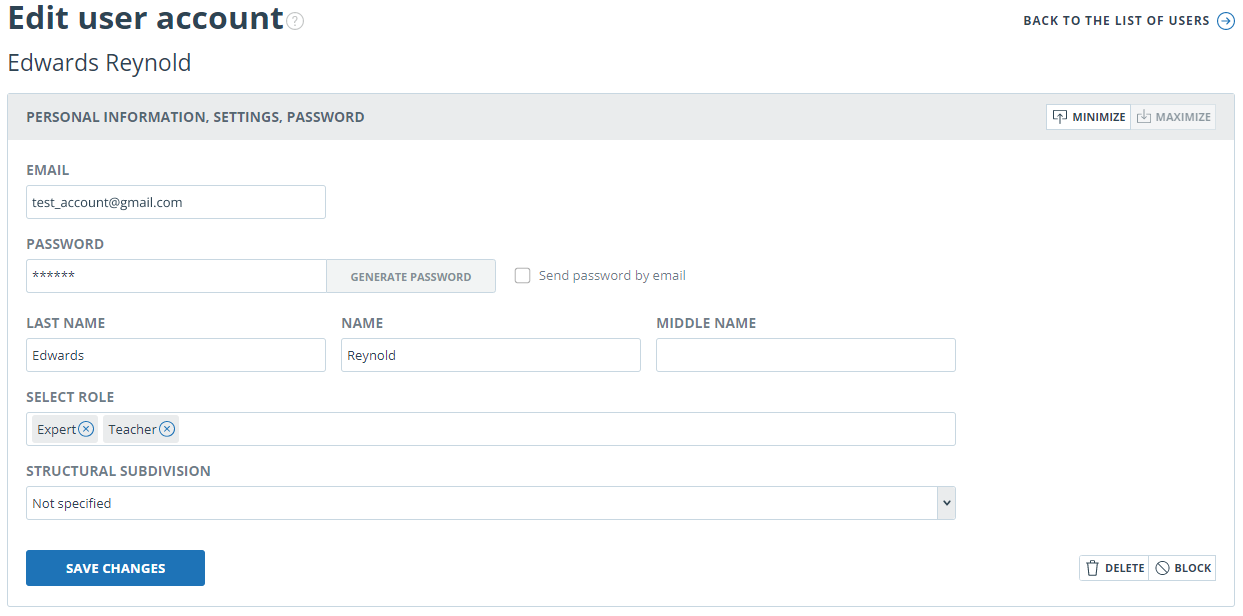
To send a password setting link to the user's e-mail, flag the box "Send password to e-mail" in the edit tab of the user’s account and click on the button "Save changes".
Please note that after sending a link to the user for setting a new password, the login using the user's current password is blocked. The user must independently set a new password to continue working in the system.
You can send links to the password setting page to multiple users at the same time. To do this, flag those users in the list who need to set a new password (if necessary, select all users) at once), and in the top menu click on the button "Send password by e-mail".
After confirmation, an informational message will appear about the successful sending of letters with links to the users’ e-mails with an indication of their number.
Please note that passwords for some system users cannot be changed (root administrator, system support service).
Blocking and deleting users
You can use the menu above the list of company's users to block and delete the user's account. On the same form, you can restore and unblock the user.
To block/delete several users at the same time, you need to mark appropriate users and click on the "Block" button or "Delete" button.
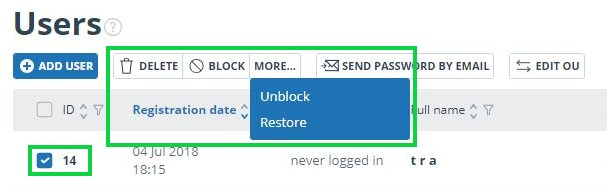
To block / delete all users on the current page, flag the ID box and click on the "Block" button or the "Delete" button.
To block / delete all users, click on "Select all users", and then on the "Block" button or on the "Delete" button.
To deselect users, click on "Deselect". In this case, all users will be deselected.
By default, the user list displays only activated users. To see deleted or blocked users, click the filter icon next to the "Status" column, select the status "blocked" or "deleted" and then click "Apply".
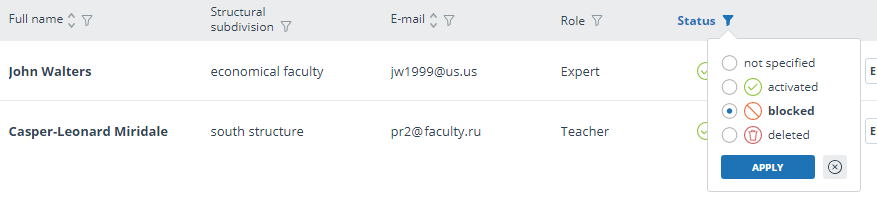
Mark appropriate users, click on the "More" button and select the "Unblock" or "Restore" action.
Company profile
The company administrator can view the company profile. To do this, in the upper right corner click on the "Menu" icon and go to the "Company profile" tab. The company profile consists of the following tabs: "Account data", "Notification settings", "Contacts", "Statistics" and "Billing".
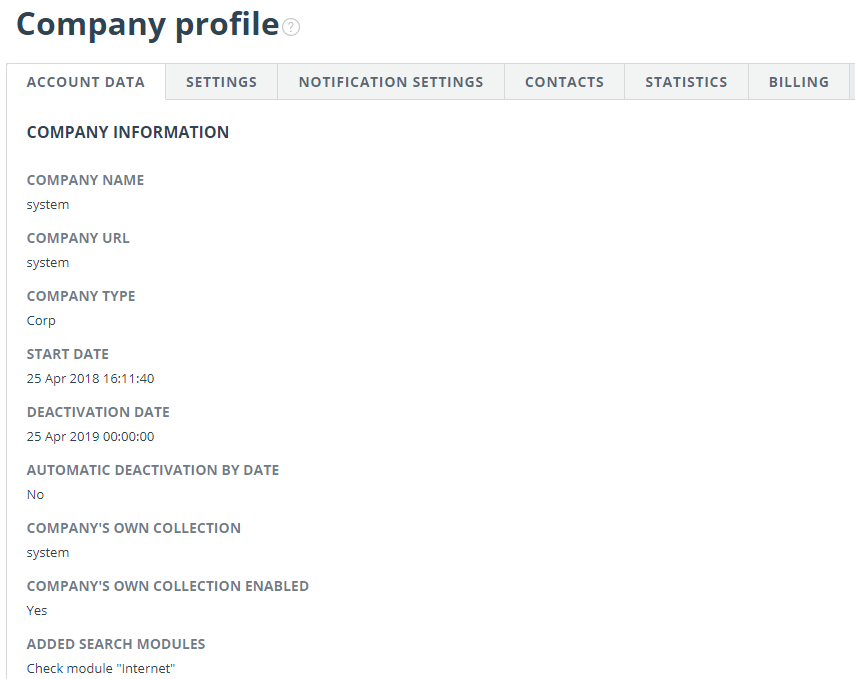
Review of account data
"Account data" tab displays information about company, information about available search modules and about company’s own collection, dates of activation and deactivation and e-mail of the root administrator of company.
This tab is not editable by company administrator. If you find a mistake or want to change information on this page, contact our Customer Care Service (support@)
Settings
On the "Settings" tab you can opt to prohibit student's self-signup. In this case, students of your organization will not be able to register in the system on their own.

Notification settings
In the "Notification settings" tab you can specify whether to notify when the limits are reached and select the timeframe of notification, and a specific date of notification. The system also has the ability to display a message and a warning about deactivation on the main page of the system.
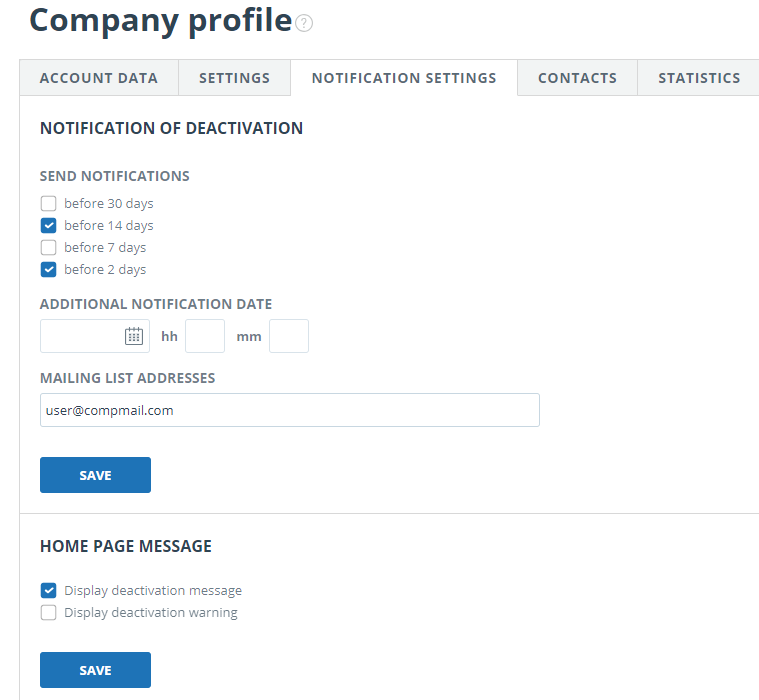
By default, the notification setting is set for 14, 2 days and at the time of shutdown. You can change the default settings, change e-mail for sending notifications, and enter an additional notification date. In the field "Mailing list addresses" you can enter several e-mails, without spaces through the separator ";".
Please note that sending notification at the moment of deactivation is mandatory and cannot be edited.
You can mark or unmark the output of the shutdown message and the company's shutdown warning on the company home page. By default, "Display deactivation message" is selected.
To save your changes, click "Save".
View and edit contact information
The "Contacts" tab displays contact information of the company administrator.
The "Contacts" section is filled with the information specified in the contract. This field is not editable by the administrator. To make changes, please contact our Customer Care Service (support@ . ).
In the "Additional contacts" section you can enter additional contact information in the edit field. To save your changes, click "Save".
Usage statistics review
To view system statistics usage please go to the page "Statistics" by clicking on the respective section of "Menu". This page displays the date of the most recent update of statistics and a statistical report by companies, aimed to assess the extent of system utilization and monitor the number of checks within one company.
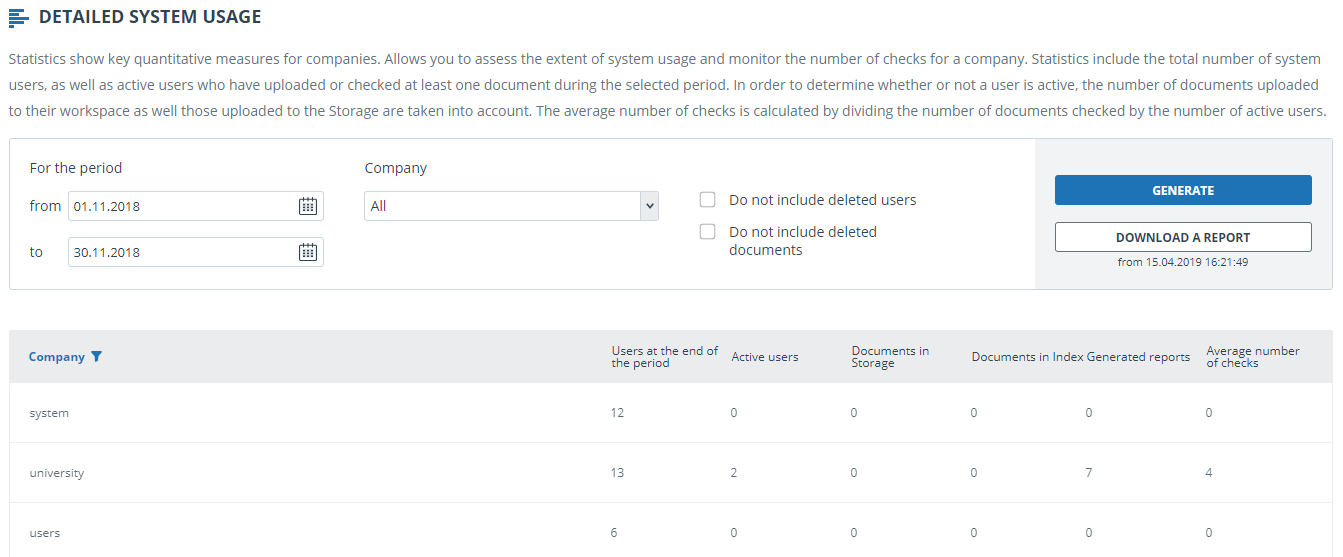
To generate the statistical report, select the time period for which you want to build a report, and click on the "Generate" button.
To view the actual data without taking into account deleted users and/or documents, mark the box next to " Do not include deleted users" and/or "Do not include deleted documents".
The following metrics are displayed in the generated statistical report:
- Users at the end of the period. The number of users created in the company from the very beginning till the end date of the selected interval.
- Active users. The number of users who have uploaded or checked at least one document during the selected period.
- Documents in Storage. Number of documents uploaded to the Storage during the selected period.
- Documents in Index. Number of documents added to the Index during the selected period.
- Generated reports. Number of text reuse reports generated during the selected period.
- Average number of checks. Number of checked documents divided by the number of active users.
Please note: Documents which are in the process of indexing are not included in the statistics.
In addition to viewing the statistical report on the website, there is the ability to download a report in csv format. To do this, click on the "Download a report" button.